With access to justice becoming a growing problem in Canada, as more people and companies become unable to afford to litigate, or be litigated against, lawyers and governments are turning to technology to find ways to bring down the costs of litigation and of prosecution. Covid-19 has forced us to accelerate the use of technology in our courts with virtual hearings, and much of the practice of litigation has moved to remote environments.

in several M&A deals, shows that decision making is clustered.
Those are not the only changes taking place in respect of litigation and technology. In order to remain competitive and increase client value, litigators are using new technologies, including legal analytics, which is growing in popularity in major litigation centres.
Analytics capabilities and tools are available in an increasing variety for various aspects of the litigation process. Technology that maps out decision trees for clients is one such example of a solution provided by a magic circle firm. Its legal tech enables clients to tap into firm databases where simple predictive AI assesses the viability of commencing litigation before deciding to proceed, helping to make litigation more cost effective and providing a broader service to clients.
Network science
Another powerful analytics tool is the network analysis branch of network science.
Although used historically and primarily by law enforcement and the intel community for mapping and dismantling terrorist and organized crime networks, network analysis technology is an ideal tool for almost any aspect of the legal process.
Network analysis identifies key players, and gatekeepers, highlights subgroups within a network and identifies individuals who call the shots. It can be used to prove or disprove a set of facts during an investigation or a trial, and as a tool for deeper analysis. Because it can be deployed to prove or disprove a set of facts, its benefit applies to defense or plaintiff counsel.
It can also be a powerful litigation analysis tool particularly for M&A deals where the network and the activities are transnational and involve hundreds of actors. Network analysis also reveals previously unobserved associations of actors within a network and identifies gaps to prioritize investigation efforts.
Centrality of actors
Network analysis uses concepts of centrality (i.e., degree, closeness, betweenness and eigenvector), brokers and density. These are mathematical determinations used to measure things like network typology, degree centrality and influence of certain actors over outcomes.
But it does more than that. The data can be used to calculate links, the strength of relationships, weakness in organizational infrastructure, money movement routes, and much more.
For example, the evidence in connection with a group of individuals, companies, and firms engaged in M&A deals involving suspected bad conduct might involve 500 different nodes and relationships by the time an investigation has concluded. Among the maze of 500 nodes and relationships, the litigator or enforcement agency needs to find out who the key actors are.
All networks have certain key actors. They control something of value – the documents, bank accounts, financings, connections, information or the process – which gives them power in the network to drive an outcome.
If the actors in the network have a criminal or fraudulent intent, the key actors act in furtherance of that goal. Sometimes only a few actors have a criminal or fraudulent intent in a network and network analysis reveals that as well because it can reveal breakages from the network by non-bad actors who break away from the network and disassociate. Bad actors only use people they trust in the commission of bad acts and a break-away actor demonstrates something about the functioning and activities of the network for further inquiry.
In financial crime or fraud cases, key actors tend to be the ones who financially profit the most from network activities. Using betweenness in network science against the network data, can reveal deeper and more accurate information about aspects of a case that lead to financial benefits by tracking linkages from actors to financial intermediaries.
Data preparation, inputs
Two legal persons that we looked at presented with typologies of being potentially problematic. A network analysis showed that they had connections in 8 countries but interestingly but only one professional gatekeeper used by both. A concentration of control in one gatekeeper is an important reveal from network analysis.
Mapping out their combined network took a long time because, in this case, analysts had to research and identify, as well as verify, the accuracy of over 314 legal and natural persons and plot the connections between them.
Ultimately, we created the network below (which is anonymized for this purpose).
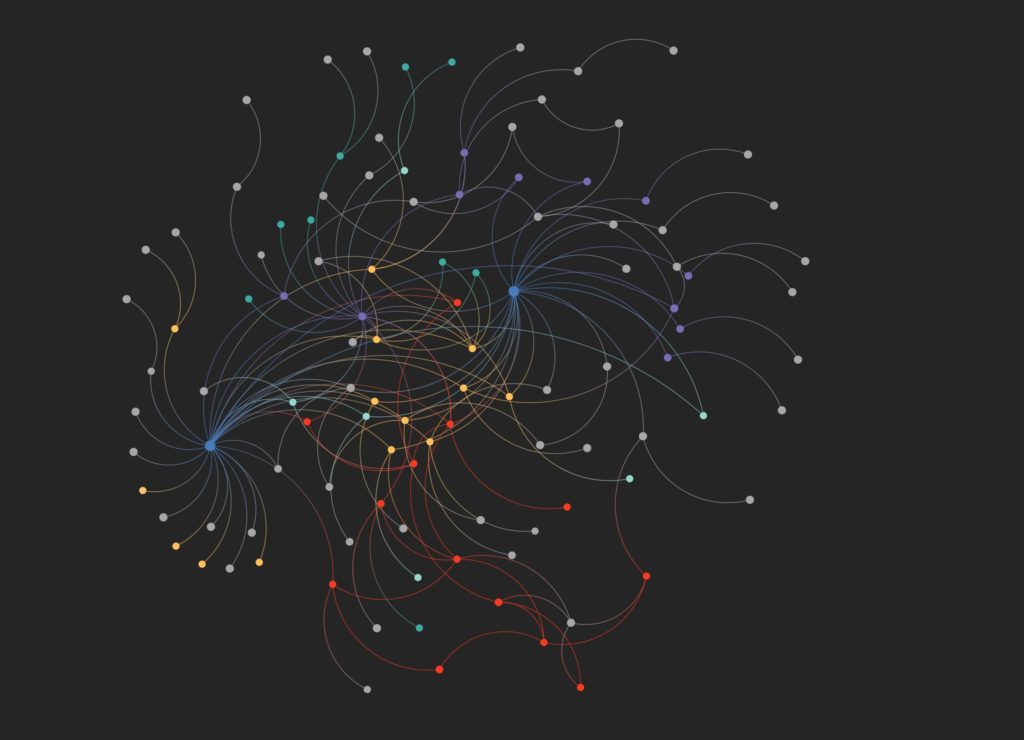
two legal persons engaged in problematic activities.
In the network above, the two legal persons are the two blue nodes.
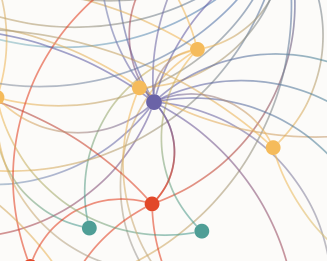
The red nodes represent the key group that directed the activities of both companies.
The one purple node in the centre between the two legal persons represents a professional gatekeeper which the key red node group appears to have used.
connected to other key nodes.
Identity of co-offenders
The yellow nodes in the network are what can be used for betweenness centrality; applying that analysis led to one central figure through which many of the activities flowed. Interestingly, it also led to a third legal person with co-offenders, demonstrating that network analysis has an added benefit – one case of network analysis can lead to revealing co-offenders which can lead to identifying other cases in which the natural persons are involved.
In the non-anonymized version of the network, all the nodes are identified and labeled and ergo, an analyst or the ultimate client knows at a glance who is connected to whom and how the network functions.
Using network analysis as a litigation or investigation tool requires data accuracy and standardization of raw data to conduct legal and criminal analysis and yield a network result that can be relied upon. Standardization also ensures that when analysts exchange analytical products for a case, which happens from investigator to regulator, law firm or enforcement agency, the data has the same meaning and is interoperable.
Once verified data sets are entered consistent with criminal analysis standards for network science, and parties use network analysis tools to identify the structure and control of a network engaged in alleged wrongful conduct, law enforcement, a regulatory body or a litigant can use the intel to disrupt the network by focusing on the key decision-makers and thereby, prevent problematic actors from future harm.